In today’s hyper-connected world, learning how to protect your privacy online and keep your online identity safe is vitally important. Whether it’s your personal emails or crucial business accounts, your data is always at risk of being exposed or stolen.
The state of cybersecurity is alarming, with sensitive user data being leaked in “data dumps” regularly. You might think you’re safe from hackers, but even if you’re not directly targeted, you could become collateral damage in a larger attack.
At Sipod, we take cybersecurity seriously, ensuring that our employees are equipped with the best tools and practices to protect both company and personal data. This guide on cybersecurity best practices for employees walks you through essential security practices to protect your accounts and data. While no method can guarantee 100% safety, following these cybersecurity tips for employees will significantly reduce the chance of becoming a target of malicious attacks.
Key Concepts in Cybersecurity Best Practices for Employees
Before we jump into the practical steps, it’s important to understand a few key principles that form the foundation of cybersecurity. Your email address, phone number, and the devices you rely on are more than just tools—they represent the backbone of your online identity. If any of these are compromised, your entire digital presence, including access to essential services, can be at risk.
To safeguard your online identity, you need to:
- Maximize security for every service you use: Ensure that every online account, from email to cloud storage, is protected with the highest security settings available.
- Know your recovery options: Familiarize yourself with how to regain access to your accounts in case they get locked or compromised.
With these key concepts in mind, let’s dive into a basic cybersecurity small business checklist to help you secure your accounts and protect sensitive data.
Getting Started: The Basic Cybersecurity Checklist
Following cybersecurity best practices for employees helps secure personal and business accounts from potential threats.
Set Up an Authenticator App
The first step in boosting your security is to install an authenticator app. These apps provide an additional level of security by generating time-sensitive codes that only you can access. We recommend either Google Authenticator or Microsoft Authenticator, as both are widely supported and user-friendly.
Pro tip: If you’re using a Microsoft account, you’ll need the Microsoft Authenticator.
Use a Password Manager
Password managers are a game-changer for managing strong, unique passwords across all your accounts. A good password manager syncs on all your devices, making sure you can access your passwords at any time, whether on your phone or computer.
When choosing a password manager, prioritize one that works on both your phone and desktop, offering seamless synchronization and convenience.
Here’s how a password manager simplifies your life:
- You only need to remember one master password.
- It generates complex, unique passwords for each account.
- It helps you avoid the all-too-common mistake of reusing passwords.
Tip for creating a strong master password:
Pick 3-4 unrelated words that are easy to remember, capitalize the first letter of each word, and sprinkle in a few numbers for extra security. This password should be one you’ve never used before!
Passwords: The First Line of Defense
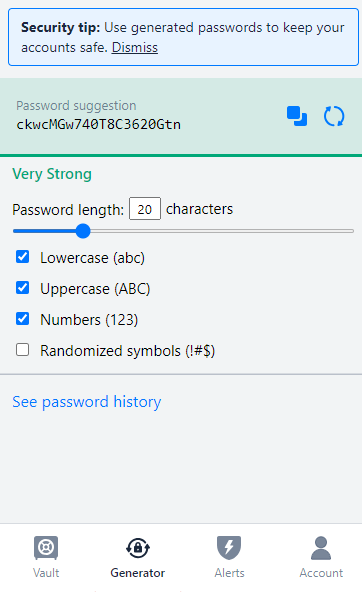
Let’s talk about passwords. Now that you’re using a password manager, every password for every service should be unique and complex. It’s easy to be tempted to reuse the same password for multiple accounts, but doing so leaves you vulnerable to attacks if even one account gets compromised.
The majority of password managers can generate strong passwords for you. To maximize security, set the parameters to incorporate a combination of numbers, uppercase and lowercase letters, and special characters.
Enable Multi-Factor Authentication (MFA)
Multi-factor authentication (MFA) is an easy but highly effective way to protect your accounts. It introduces an extra step to the login process—usually a code from an app or SMS—so even if someone has your password, they won’t be able to gain access to your account without the second layer of authentication.
Here’s what you need to do:
- Enable MFA on every service that supports it.
- Save backup codes in a safe place by printing them out and storing them securely.
If you lose your phone, those backup codes are your lifeline for account recovery. And remember, once you set up MFA, most services will log you out of current sessions to ensure you’re logging back in securely.
Securing Your Most-Used Accounts
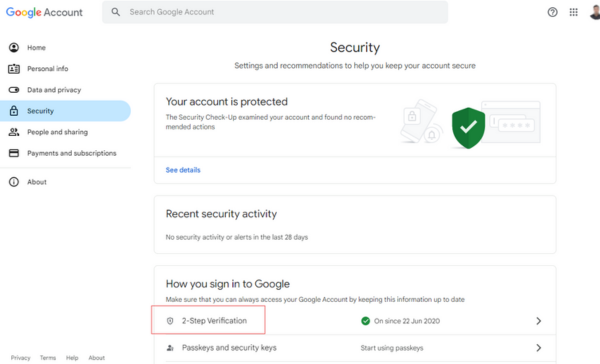
To enable two-factor authentication on Google, visit Google Account Security and follow the steps.
Microsoft (DevOps, Azure Portal)
If you use Microsoft accounts, two-factor authentication should be enabled by default. If not, log in to your account and navigate to the security settings here.
Atlassian
To secure your Atlassian account, head over to Atlassian Security.
GitHub
To secure your GitHub account, go to GitHub Security and enable two-factor authentication.
Slack
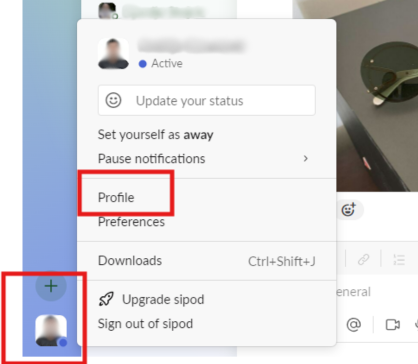
For Slack, click on your profile picture in the app, select Profile, and then navigate to Account Settings.
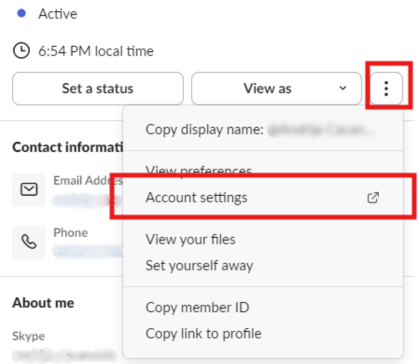
Your default browser will open the Slack Account page. From there, you can set up two-factor authentication.
Protecting Your Devices
Securing your accounts is just one part of the puzzle; your devices need protection, too.
Computer Security
- Set a password or PIN for logging in.
- Avoid auto-login on any device—especially laptops—to block unauthorized access in case your device gets lost or stolen.
- Install security updates immediately when they become available.
For most users, Windows Defender provides adequate protection. However, consider a paid antivirus if you frequently visit questionable websites or plug in unverified USB devices.
Securing Your Phone
Your phone should always be locked with a password, pattern, or biometric data (such as fingerprint or facial recognition). This safeguards against unauthorized access in case your phone is lost or stolen.
Final Thoughts: Staying Vigilant
No security solution is foolproof, but following these steps significantly increases your protection against data breaches and hacking attempts. Remember to regularly check your email on sites like haveibeenpwned.com to see if any of your accounts have been compromised. Adopting cybersecurity best practices for employees requires staying informed and vigilant against potential cyber threats.
Tags:


